Changes have been made to the individual login, registration and database views dashboards in order to have shorter load time.



Changes have been made to the individual login, registration and database views dashboards in order to have shorter load time.



Previously, all users registered in any DeepKnowledge portal could not register again in any other portal using the same email address.
We have acknowledged feedback from our customers and have changed that behavior to allow the same users to register into multiple DeepKnowledge portals provided they are part of the relevant organizations.
Library administrators can now create subfolders to organize library documents.
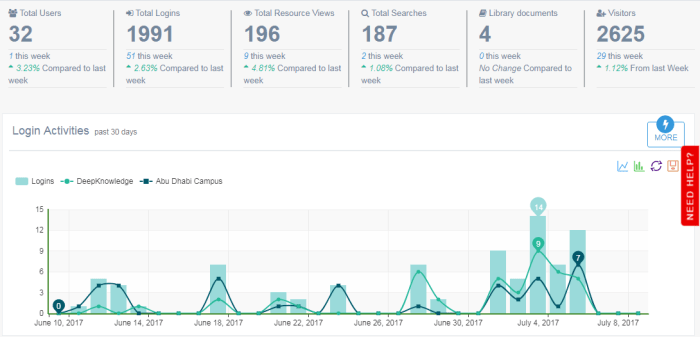
You can now navigate from the main Dashboard on the control panel to dedicated dashboards showing detailed information about certain key aspects of the library usage, including the logins, the registrations and the resources usage.
A full-fledged library catalog application is now available as an optional module that can be activated by administrators and includes library management, ISBN lookup, catalog population via MARC/MARCXML, extensive lending, holdings, circulations statistics and over 360 million catalog records available from OCLC’s WordlCat and Google Books Services.
The ChatBot is your virtual assistant, it recognizes natural language and can answer over 10,000 questions related the way the e-library control panel and the various apps can be used.
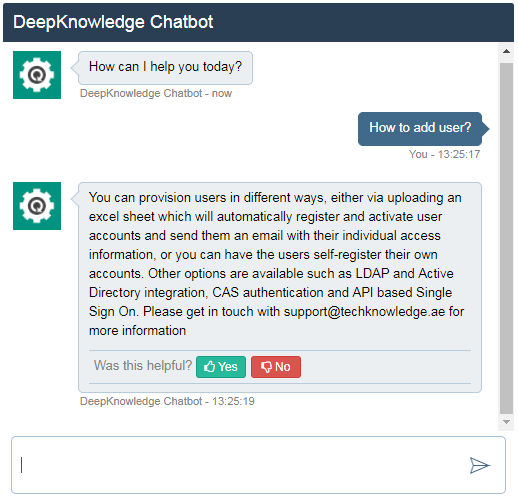
A new ChatBot will be released soon for end-users (non-admins) as well in order to answer their most commonly asked questions regarding content access, search, account information and library portal features.
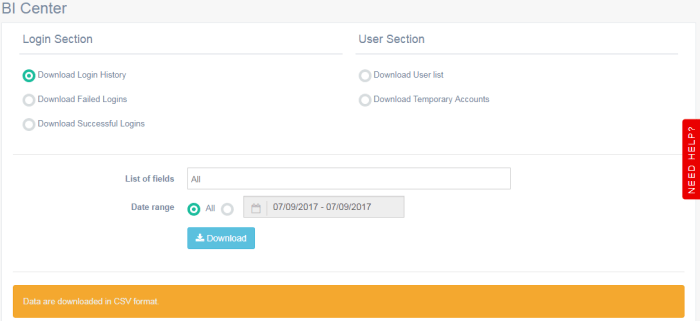
The BI Center (Business Intelligence) is where you can export in CSV format your usage counter data in a raw format, which can be imported back into your own specialized statistics and data mining software for further analysis.
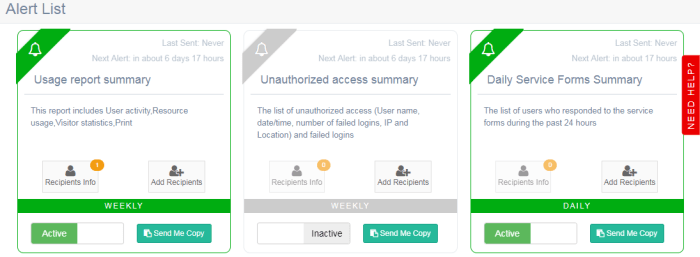
The email alerts have been redesigned from the ground up to reflect a modern look and focus on the most important key indicators and allow you to quickly get the information you need without having to scroll through multiple pages of information.
Libraries can now setup guest access within their IP range perimeter and campus in order to provide one-click access to their electronic resources, which does not require user account registration or login
For more information, please get in touch with support@techknowledge.ae to know more
As part of our ongoing efforts to improve the security in the services delivered through the DeepKnowledge Library Management Platform, we are pleased to announce that we have partnered with Arbor Networks, a leading internet security firm, in order to further strengthen our network and applications security
DDos stands for Distributed Denial of Service, which is a technique malicious entities use to flood network infrastructure and target websites with a large amount of traffic distributed over a large amount of infected machines across the world in order to slow down access. The mitigation service we have put in place automatically detects these types of attacks and re-routes malicious traffic into different scrubbing networks, which enables the online services to remain online and unaffected
The following Diagram describes the extra 3 protection layers we have put in place recently

In today’s word and the current security context and landscape, protection against all types of attacks and intrusions is critically important for any online service, and we at DeepKnowledge consider security at the top of our priorities
Some of the immediate benefits of the enhanced security services are
Multi-layered protections
The network is secure with layered protections, from network wide packet scanning, through granular traffic analysis, down to server-level anomaly detection, for the most comprehensive protection against volumetric DDoS attacks, network and session layer attacks, DNS attacks, and more.
Avoid Downtime
The network is secure with layered protections, from network wide packet scanning, through granular traffic analysis, down to server-level anomaly detection, for the most comprehensive protection against volumetric DDoS attacks, network and session layer attacks, DNS attacks, and more.
Immediate Response
DDoS specialists we work with stay ahead of ongoing or imminent DDoS attacks with on-premises detection and 24x7x365 traffic monitoring to initiate mitigation measures and take the necessary actions when anomalous traffic is identified
In technical terms, the following types of DDoS can be detected
CGI request, denial of capability, diluted low-rate degrading, direct, DNS request attack, high-rate, disruptive, hybrid attack, ICMP attack, isotropic attack traffic distribution, land attack, Xmas tree, mail bomb, non-isotropic attack traffic distribution, ping of death, reflector, TCP reset, TCP SYN flooding, TCP SYN-ACK, TCP URGPSH, TCP idle attack, CC attack, teardrop attack, HTTP GET floods, HTTP POST floods, SIP invite floods, UDP flooding, URL flood, LOIC and HOIC DNS/NTP/SSDP/RIPv1 and other reflection/amplification attacks, slow POST, varied rate, using regex filters
Please contact our support team at support@techknowledge.ae and we will respond to all your questions
You must be logged in to post a comment.